Social Engineering & Statistics
Cyber crime is a growing concern in today’s digital age, and social engineering or psychological manipulation is a tactic that is increasingly being used by cyber criminals to carry out their attacks.
According to a report by the FBI, social engineering was the leading method used in cyber crime incidents in 2019, accounting for over half of all reported incidents. This includes tactics such as phishing, pretexting, baiting, and scareware, which all rely on manipulating the victim’s emotions or trust in order to gain access to sensitive information or systems.
 Social Engineering
Social Engineering
Social Engineering & Attack Types:
Social engineering is a tactic that relies on psychological manipulation to influence individuals to divulge sensitive information or perform actions that may not be in their best interests. It is a common tactic used by cybercriminals to gain access to sensitive data or systems.
There are many different types of social engineering attacks, and they can take many forms. Here are a few examples
Phishing attacks: These involve sending fake emails or text messages that appear to be from a legitimate source, in an attempt to trick the recipient into revealing sensitive information or visiting a malicious website.
Baiting: This involves offering something that the victim wants, in exchange for information or access to a system.
Scareware: This involves tricking the victim into believing that their computer is infected with a virus or malware, and then offering to sell them software to fix the problem.· Impersonation: This involves pretending to be someone else, in order to gain access to sensitive information or systems.
Pretexting: This involves using a fake identity or pretext in order to obtain sensitive information.
Influence: This involves using psychological manipulation techniques to influence the victim’s decision-making.
Physical coercion: This involves physically forcing the victim to divulge sensitive information or take a certain action.
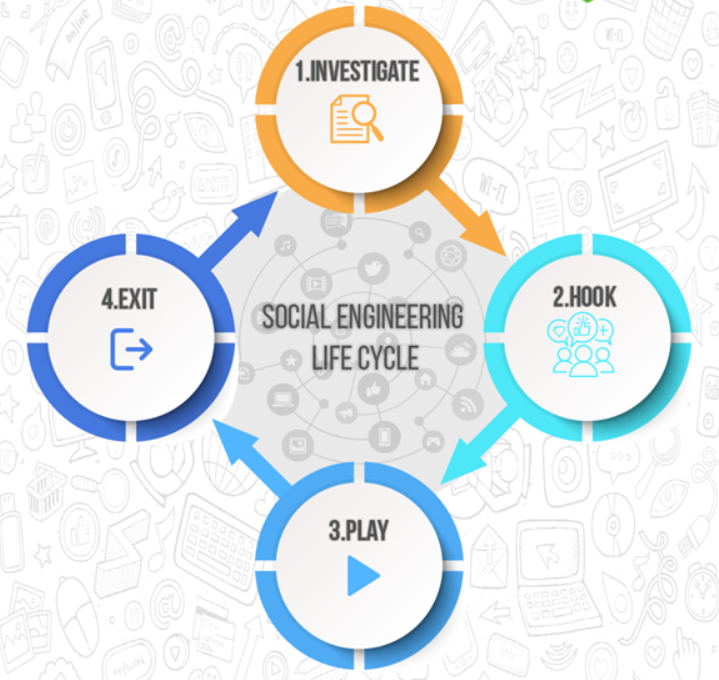 Attack Cycle
Attack Cycle
Cases of Social Engineering Attacks:
A high-profile cyber crime that was carried out using social engineering tactics is the 2017 Equifax data breach. In this case, attackers exploited a weakness in the company’s website software to gain access to the personal data of 147 million people. The attackers used phishing emails to trick Equifax employees into revealing their login credentials, which allowed the attackers to gain access to the company’s systems and steal the sensitive data.
Another example of social engineering being used in a cyber crime is the WannaCry ransomware attack that affected thousands of businesses and organizations in 2017. In this case, the attackers used baiting tactics, offering a fake software update that, when downloaded, installed the ransomware on the victim’s system, locking them out of their own data unless they paid a ransom.
Another example of a social engineering attack by email is the phishing attack that targeted Google and other tech companies in 2010. In this case, the attackers sent phishing emails to employees at the companies, purporting to be from the HR department and requesting that the employees update their personal information. The emails included a link that, when clicked, took the employees to a fake website where they were prompted to enter their login credentials. The attackers were able to steal the login credentials of more than 30 employees at Google and other tech companies, allowing them to gain access to the companies’ systems and steal sensitive data.
This attack highlights the importance of being cautious when receiving emails requesting personal information or login credentials, and the need to verify the authenticity of such requests before responding.
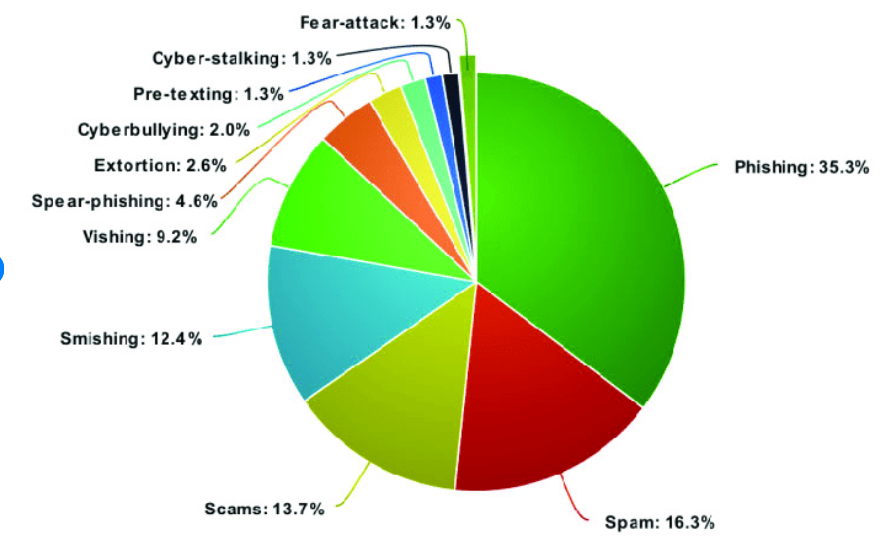 Attack Breakdown
Attack Breakdown
Psychological stress as a catalyst to Attacks.
It’s true that social engineering attacks often rely on psychological manipulation to be successful, and stress at work and in personal life can make individuals more vulnerable to these tactics. When people are under stress, they may be more likely to make impulsive decisions or to overlook warning signs that might normally alert them to a potential threat.
For example, a cyber criminal may send a phishing email to an employee who is under stress, pretending to be from their boss or HR department and requesting sensitive information. If the employee is distracted or overwhelmed, they may be more likely to quickly respond to the email without verifying its authenticity, potentially falling victim to the attack.
Steps to reduce Social Enginerring Attacks:
There are several steps that individuals and organizations can take to protect themselves from social engineering attacks:
Educate employees: Ensure that all employees are aware of the risks of social engineering and the importance of being cautious when interacting with unfamiliar individuals or receiving suspicious emails or messages. Conduct regular training sessions to keep employees up to date on the latest tactics being used by cyber criminals.
Use strong and unique passwords: Use passwords that are difficult for attackers to guess and avoid using the same password for multiple accounts.
Enable two-factor authentication: whenever possible to add an extra layer of protection.
Implement security measures: Use security software, such as antivirus and firewall programs, to protect against malware and unauthorized access. Keep all software and security measures up to date to ensure the best protection.
Provide resources: It’s also important for organizations to provide resources & support to help employees manage stress and maintain a healthy work-life balance, which can help reduce their vulnerability to social engineering attacks.
Verify the authenticity of requests: for sensitive information: Be cautious when receiving requests for sensitive information, such as login credentials or personal data, and verify the authenticity of the request before responding.
Stay vigilant: Be cautious when clicking on links or downloading attachments: Be careful when clicking on links or downloading attachments, as these can be used to install malware or trick you into revealing sensitive information.
Best Practice:
Looking at the statistics and the need to tackle with psychological manipulations. It is hard to overcome the manipulations in the near future as to it requires educating employees and their own awareness to such incidents, but in a race of delivering deadlines it often comes to the last priority. For today the best posssible way to tackle such attacks and various other types to protect organizations from any kind of breach.It is advisable to implement security controls in their ecosystem providing security from their endpoints to the network perimeters.
Having tons of commercial security solutions in market available organizations can go for them as which suits best for their need.
But for Home Network we’ll be having complete implementation tutorial on CyberTab of various Open Source tools available for free to protect your network.
Till then stay vigilant and don’t fall into any Cyber Trap.
Don’t forget to:
1
sudo apt update && sudo apt upgrade
Stay Updated.
